Running a DNS stealth master
A foreword by Per-Olov Sjöholm
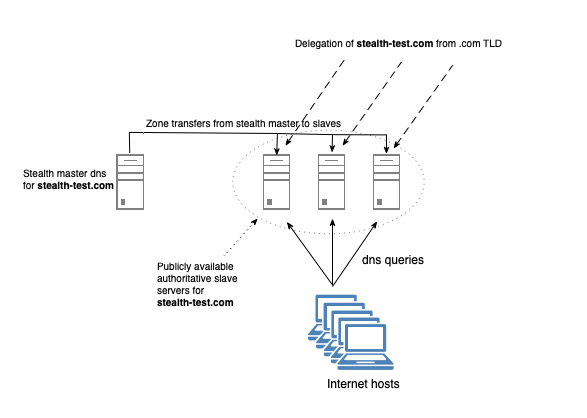
What is a stealth master DNS
A stealth master DNS, also known as hidden master DNS, is a configuration where the primary authoritative DNS server for a domain is intentionally kept hidden from public view. In a typical DNS setup, both the primary (master) and secondary (slave) DNS servers are publicly visible and accessible to anyone querying DNS records. However, in a stealth master DNS configuration, the primary DNS server is not publicly listed in the domain’s DNS records and is not directly accessible to external queries. Instead, the primary DNS server communicates only with secondary DNS servers, which then respond to DNS queries from clients.
What are the benefits
Flexibility:
If the stealth master dns is moved or renamed, you only have to tell the slaves to fetch from another server and no delegation change work at the registrar. From a private (i.e no business) perspective you can run a stealth master at home, and easily move it later to let say a VPS in the cloud. And when you do, there won’t be any work at the registrar with delegation changes. Aside from the flexibility described above, there are as well many other reasons to have a stealth master DNS. Below are two more benefits.
Enhanced Security:
Stealth master DNS setups provide an additional layer of security by hiding the primary DNS server from public view. This can help mitigate direct attacks on the primary DNS server, as potential attackers won’t have visibility into its existence or location.
Facilitation of DNSSEC Implementation:
Concealing the primary DNS server can simplify the implementation of DNS Security Extensions (DNSSEC), which add cryptographic authentication to DNS responses. With a stealth master DNS setup, organizations can focus on deploying and managing DNSSEC without exposing sensitive cryptographic keys or DNSSEC-related infrastructure to potential threats. A well set up stealth master dns is often seen as an acceptable trade off regarding security for storing the dnssec private keys. The other option would otherwise be to buy a very expensive Hardware Security Module (a.k.a HSM).
What does it mean technically
Technically this means that you carry out these tasks:
When you do the delegation from the TLD, you delegate your dns domain to the public secondary slave servers and exclude your stealth master dns server.
In your dns config file you:
Allow slave dns servers to transfer your zones, either by IP acl or by TSIG keys. TSIG key is preferred as the slave dns servers then can swap IP addresses without breaking the transfer.
In your zone file that you edit in the stealth master host you:
list only the public slave servers and NOT the stealth master name server itself.
usually also set the host in the SOA record to one of the slave servers.
This way the stealth master dns server is totally invisible to the public internet.